Ataques de envenenamiento SEO: Cómo los ciberdelincuentes se aprovechan de los resultados de las búsquedas
Información clave
- Los ataques de envenenamiento SEO han aumentado un 60% en seis meses, con más de 15.000 sitios comprometidos en importantes campañas dirigidas a usuarios empresariales.
- Las campañas actuales de octubre de 2025 incluyen la Operación Rewrite ( malware BadIIS), herramientas de administración troyanizadas que afectan a más de 8.500 sistemas y ataques de suplantación de identidad de herramientas de inteligencia artificial.
- Las amenazas combinan el compromiso de sitios legítimos con contenidos generados por IA para crear resultados de búsqueda maliciosos convincentes que eluden la seguridad tradicional.
- La detección requiere un análisis del comportamiento más allá de las defensas perimetrales, ya que los atacantes explotan los resultados de confianza de los motores de búsqueda y los dominios de apariencia legítima.
- Las estrategias de defensa específicas de cada sector son esenciales, y los sectores sanitario, jurídico y financiero se enfrentan a campañas selectivas que utilizan palabras clave verticales específicas.
Cada día, miles de millones de usuarios confían en los motores de búsqueda para que les guíen hacia recursos legítimos, y los atacantes han convertido esa confianza en un arma. La mecánica es insidiosa: los sitios maliciosos alcanzan las primeras posiciones en descargas de software, documentación técnica y herramientas empresariales, a la espera de que las víctimas busquen su camino hacia el compromiso. En octubre de 2025, esta explotación de la confianza implícita había alcanzado proporciones de crisis, con investigadores de seguridad descubriendo más de 8.500 sistemas comprometidos a través de una sola campaña dirigida a administradores de TI que buscaban descargas de PuTTY y WinSCP, parte de un aumento del 60% en los ataques de envenenamiento SEO en sólo seis meses.
El envenenamiento SEO se aprovecha de una vulnerabilidad fundamental en la forma en que navegamos por Internet: nuestra confianza en los motores de búsqueda para encontrar recursos legítimos. A diferencia de los ataquesphishing tradicionales, que llegan sin invitación a la bandeja de entrada, el envenenamiento SEO espera a que las víctimas acudan a él, aprovechando el propio acto de buscar información como vector de ataque. Con 15.000 sitios comprometidos en campañas recientes y actores de amenazas que ahora utilizan IA para generar software malicioso convincente a escala, la comprensión y la defensa contra el envenenamiento SEO se ha convertido en fundamental para la seguridad de las organizaciones.
¿Qué es el envenenamiento SEO?
El envenenamiento SEO es una técnica de ingeniería social basada en búsquedas en la que los atacantes manipulan los rankings de búsqueda para que las páginas maliciosas parezcan legítimas y muy visibles en los resultados de búsqueda. La víctima hace clic en lo que parece ser un resultado fiable y es redirigida a una descarga falsa, una página de inicio de sesión para recopilar credenciales o un sitio que distribuye malware.
Es eficaz porque combina la intención del usuario con la confianza percibida. La víctima busca activamente una solución y da por sentado que los resultados mejor posicionados son seguros. Los atacantes amplifican este efecto abusando de sitios web legítimos comprometidos, utilizando el encubrimiento para mostrar contenido limpio a los rastreadores y contenido malicioso a los usuarios reales, e imitando fielmente la marca oficial y los flujos de distribución.
El envenenamiento SEO suele dirigirse principalmente a:
- Consultas sobre software y «descargas oficiales»
- Herramientas administrativas y utilidades de acceso remoto
- Flujos de trabajo de inicio de sesión y restablecimiento de contraseña de SaaS
- Soluciones técnicas específicas para casos en los que los usuarios tienen poco tiempo.
La defensa contra el envenenamiento SEO requiere algo más que listas de bloqueo. Los equipos de seguridad deben correlacionar las referencias de búsqueda con destinos riesgosos, descargas sospechosas, cadenas de ejecución anormales y comportamientos de identidad anómalos, y luego contener rápidamente cuando aparezcan indicadores de compromiso para evitar la persistencia y el movimiento lateral.
¿Cuál es el objetivo del envenenamiento SEO?
El objetivo del envenenamiento SEO es convertir el tráfico de búsqueda en un acceso fiable «en la parte superior del embudo» para los ciberdelincuentes. La mayoría de las campañas se optimizan para uno de estos cuatro resultados:
- Robo de credenciales: captura nombres de usuario, contraseñas, tokens MFA o cookies de sesión a través de páginas de inicio de sesión similares.
- Malware : Distribuir instaladores troyanizados, droppers o scripts que establecen persistencia.
- Estafas de monetización: empujan a las víctimas hacia un soporte técnico falso, fraudes de suscripción o abuso de afiliados.
- Aprovechamiento de la infraestructura: Comprometer servidores legítimos y utilizarlos como infraestructura de alojamiento, redireccionamiento o proxy de confianza para futuras campañas.
Para los defensores, la idea clave es que la manipulación del ranking es el método de entrega. El riesgo real es lo que ocurre después del clic.
La evolución del phishing tradicional
El envenenamiento SEO cambia la interacción de «empujar» a «tirar». phishing tradicional empuja un señuelo a las bandejas de entrada y espera que se haga clic. El envenenamiento SEO espera en el momento de necesidad, cuando un usuario está buscando una descarga, una solución o una página de inicio de sesión, e intercepta esa intención.
Esto cambia el problema defensivo. Los controles de correo electrónico y la formación en materia de concienciación siguen siendo útiles, pero no cubren bien los riesgos derivados de las búsquedas. Una defensa eficaz requiere: controlar la procedencia del software, supervisar las navegaciones y descargas arriesgadas derivadas de búsquedas, y detectar comportamientos posteriores al clic (uso indebido de credenciales, persistencia, movimiento lateral) que indiquen que el señuelo ha tenido éxito.
SEO poisoning frente a phishing malvertising frente a typosquatting
Estas técnicas suelen confundirse, pero difieren en cómo se crea el acceso inicial. La diferencia fundamental radica en el origen del señuelo y en cómo se dirige a la víctima hacia la infraestructura maliciosa. Ese vector de entrega determina qué controles son más eficaces.
Las campañas suelen encadenar estos métodos. El envenenamiento SEO puede generar visibilidad, la publicidad maliciosa puede amplificar el tráfico y el typosquatting puede servir como punto final para la recopilación de credenciales.
Para los defensores, la lección es operativa: el vector de entrada cambia, pero los comportamientos posteriores al clic, las descargas sospechosas, las cadenas de ejecución anormales, los mecanismos de persistencia y la actividad de identidad anómala siguen siendo la capa de detección más fiable.
Cómo funcionan los ataques de envenenamiento SEO
Los ataques de envenenamiento SEO funcionan manipulando lo que los usuarios ven en los resultados de búsqueda y controlando lo que ocurre después del clic. Los atacantes identifican consultas de alta intención, como descargas de software, búsquedas de «sitios oficiales», páginas de inicio de sesión, plantillas legales o términos de resolución de problemas urgentes, y diseñan contenido malicioso para que ocupe un lugar destacado en esas búsquedas. Dado que los usuarios tienden a confiar en los primeros resultados, esta visibilidad se convierte en un canal de distribución fiable.
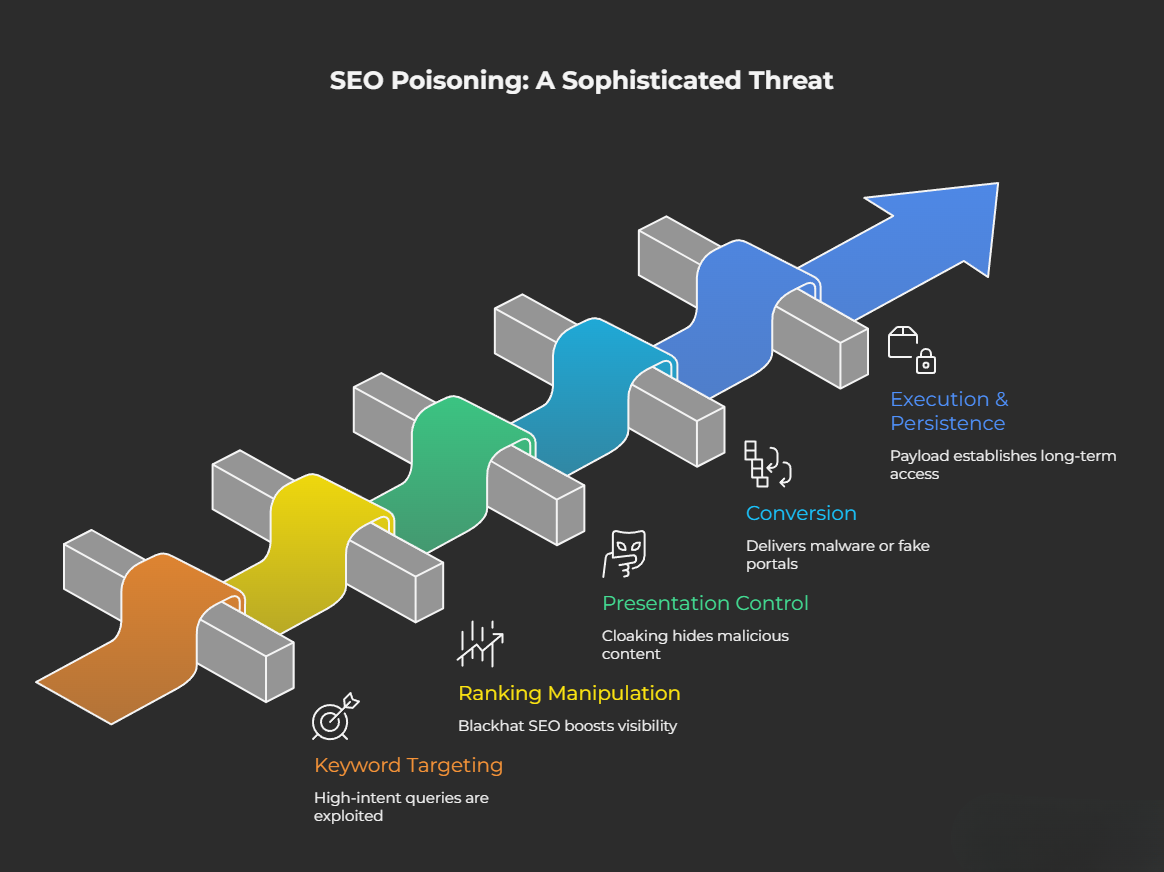
Los atacantes se basan en los mismos mecanismos de optimización que utilizan los profesionales del marketing legítimos, lo que dificulta su prevención. En lugar de explotar primero las vulnerabilidades del software, explotan los algoritmos de clasificación y la psicología del usuario.
La cadena de ataque
- Selección de palabras clave: seleccione términos de búsqueda relacionados con la urgencia, la autoridad o el acceso privilegiado (por ejemplo, herramientas de administración, clientes VPN, acuerdos legales, plantillas financieras).
- Manipulación del ranking: Utilizar técnicas de SEO blackhat para aumentar artificialmente la visibilidad. Las tácticas más comunes incluyen:
- - Relleno de palabras clave y saturación semántica de palabras clave.
- ‣ Redes de enlaces privados para simular autoridad.
- ‣ Inflamación artificial de clics para indicar popularidad.
- ‣ Comprometer sitios web legítimos para heredar la confianza del dominio.
- - Relleno de palabras clave y saturación semántica de palabras clave.
- Control de presentación: utilice el cloaking para mostrar contenido benigno a los rastreadores de búsqueda, mientras que se muestran páginas maliciosas a los usuarios reales. Los scripts de huellas digitales pueden adaptar las cargas útiles en función del navegador, la ubicación geográfica o el dispositivo.
- Conversión: Entregar un instalador de software troyanizado, un portal de inicio de sesión falso o una cadena de redireccionamiento que termina en la recolección de credenciales o malware . Los dominios con errores tipográficos a menudo refuerzan su legitimidad al parecerse mucho a marcas de confianza.
- Ejecución y persistencia: una vez descargada, la carga útil puede establecer persistencia, robar credenciales del navegador, implementar cargadores secundarios o crear canales de comando y control salientes. Dado que el usuario inició la descarga, es posible que las defensas perimetrales tradicionales no detecten inmediatamente la actividad.
Las campañas de envenenamiento SEO suelen adaptarse a sectores y funciones específicos. Los profesionales del ámbito jurídico pueden encontrarse con búsquedas envenenadas de «plantillas de contratos», los administradores de TI pueden ser blanco de instaladores falsos de herramientas de administración y los usuarios del sector financiero pueden verse atraídos por documentos relacionados con la normativa o el cumplimiento.
Para los defensores, la técnica de clasificación puede variar, pero la secuencia posterior al clic sigue siendo la misma:
Búsqueda de referencias → destino sospechoso → descarga o inicio de sesión → ejecución anómala o uso de credenciales → persistencia. Esa cadena de comportamiento es la superficie de detección más estable.
¿Por qué esto se amplía?
El envenenamiento SEO se extiende porque la manipulación del posicionamiento y la generación de contenido pueden automatizarse. Los atacantes pueden publicar, probar, rotar y sustituir señuelos rápidamente. La infraestructura comprometida proporciona confianza integrada, mientras que el encubrimiento reduce la detección por parte de los sistemas de escaneo estático y de reputación.
El efecto neto es significativo desde el punto de vista operativo: la búsqueda se convierte en un canal de acceso inicial renovable que los atacantes pueden repetir más rápido de lo que los controles estáticos pueden bloquear. El señuelo específico puede cambiar a diario, pero la secuencia posterior al clic, la referencia de búsqueda, la descarga o el inicio de sesión sospechosos, la ejecución anómala, el uso indebido de credenciales y la persistencia siguen siendo constantes.
Para los defensores, esa coherencia es el punto de control. La detección debería centrarse menos en predecir qué resultado de búsqueda es malicioso y más en identificar la cadena de comportamiento que se produce cuando el señuelo tiene éxito.
Tipos de ataques de envenenamiento SEO
El envenenamiento SEO abarca múltiples metodologías de ataque, cada una de las cuales explota diferentes aspectos de los algoritmos de los motores de búsqueda y del comportamiento de los usuarios. Entender estas variaciones ayuda a las organizaciones a reconocer las amenazas potenciales e implementar las defensas adecuadas.
La "typosquatting" sigue siendo una de las técnicas más sencillas y eficaces. Los atacantes registran dominios que se parecen mucho a sitios legítimos, aprovechando errores tipográficos comunes o grafías alternativas. La reciente campaña de suplantación del cliente VPN Ivanti lo demostró con dominios como ivanti-pulsesecure[.]com, que parecían lo suficientemente creíbles como para engañar a los administradores de TI de las empresas que buscaban software VPN.
El relleno de palabras clave consiste en cargar las páginas con repetidas instancias de las palabras clave objetivo, a menudo ocultas para los usuarios pero visibles para los motores de búsqueda. Aunque los algoritmos de búsqueda han mejorado en la detección de esta técnica, las variantes más sofisticadas siguen teniendo éxito. Los atacantes utilizan ahora variaciones semánticas de las palabras clave, frases de cola larga y una colocación contextual de las palabras clave que parece más natural, pero que sigue engañando a los algoritmos de clasificación.
El "cloaking" representa un enfoque más técnico en el que los sitios sirven contenidos diferentes en función del visitante. Los rastreadores de los motores de búsqueda reciben contenidos optimizados, aparentemente legítimos y bien clasificados, mientras que los usuarios reales se encuentran con mecanismos de entrega de malware o páginas de phishing . La campaña de malware BadIIS ejemplifica la ocultación avanzada, con servidores IIS comprometidos que detectan los tipos de visitantes y sirven el contenido en consecuencia.
Técnicas específicas de la campaña
Los principales actores de amenazas han desarrollado técnicas de firma que caracterizan sus operaciones. Gootloader, una de las operaciones de envenenamiento SEO más persistentes, se especializa en búsquedas legales y empresariales. Su infraestructura se compone de miles de sitios WordPress comprometidos que alojan falsas discusiones en foros sobre contratos, acuerdos y documentos empresariales. Cuando las víctimas descargan estas supuestas plantillas, reciben malware Gootloader que sirve como intermediario de acceso inicial para los ataques de ransomware.
La campaña SolarMarker adopta un enfoque diferente, centrándose en descargas de software y documentación técnica falsas. Esta operación mantiene una amplia infraestructura de botnet que genera constantemente nuevos contenidos dirigidos a profesionales de TI y administradores de sistemas. Sus sitios suelen posicionarse para consultas técnicas poco conocidas en las que la competencia es menor, lo que permite que los resultados maliciosos alcancen posiciones destacadas con mayor facilidad.
La operación Rewrite, atribuida a actores de amenazas de habla china, demuestra la evolución hacia el envenenamiento SEO del lado del servidor. En lugar de crear nuevos sitios maliciosos, esta campaña compromete los servidores web existentes e instala el malware BadIIS. Este enfoque ofrece varias ventajas: autoridad de dominio heredada de sitios legítimos, clasificaciones de búsqueda existentes para secuestrar y costes de infraestructura reducidos para los atacantes.
El envenenamiento SEO en la práctica
El impacto en el mundo real del envenenamiento SEO se hace evidente al examinar las campañas actuales dirigidas activamente a organizaciones de todo el mundo. Octubre de 2025 ha sido testigo de un aumento sin precedentes de ataques sofisticados que demuestran la evolución de las tácticas y la creciente escala de estas operaciones.
La Operación Rewrite, identificada por primera vez en marzo de 2025 pero que se ha intensificado drásticamente este mes, representa una de las campañas de envenenamiento SEO del lado del servidor más sofisticadas que se han observado. El actor de la amenaza, rastreado como CL-UNK-1037 por la Unidad 42 de Palo Alto Networks, ha comprometido miles de servidores IIS legítimos en el este y el sudeste asiático, con especial atención a las organizaciones vietnamitas. El malware BadIIS desplegado en estos ataques no se limita a redirigir el tráfico, sino que actúa como un proxy inverso, interceptando y modificando el tráfico HTTP en tiempo real para manipular los rankings de búsqueda mientras sirve contenido malicioso a los visitantes objetivo.
La campaña de herramientas de administración troyanizadas descubierta por Arctic Wolf ha comprometido más de 8.500 sistemas en todo el mundo, principalmente dirigidos a administradores de TI y proveedores de servicios gestionados. Las víctimas que buscan PuTTY, WinSCP y otras herramientas administrativas se encuentran con sitios maliciosos que ocupan un lugar destacado en los resultados de búsqueda. La sofisticación se extiende al propio malware : la puerta trasera Oyster (también conocida como Broomstick o CleanUpLoader) establece la persistencia a través de tareas programadas, crea shells inversos y proporciona capacidades completas de acceso remoto. Este nivel de compromiso a menudo sirve como precursor del despliegue de ransomware, por lo que los procedimientos de respuesta rápida a incidentes son críticos.
Las investigaciones académicas que analizan el impacto financiero revelan que las pequeñas y medianas empresas sufren pérdidas medias de 25.000 dólares por incidente de envenenamiento SEO. Sin embargo, cuando estos ataques conducen al despliegue de ransomware o a importantes violaciones de datos, los costes pueden ascender a millones. Los costes de la ciberdelincuencia mundial, previstos en 10,5 billones de dólares para 2025, incluyen cada vez más el envenenamiento SEO como principal vector de acceso inicial.
Panorama actual de las amenazas (octubre de 2025)
La campaña de abuso de certificados de Microsoft Teams, desbaratada con éxito por Microsoft este mes, demostró cómo los certificados legítimos de firma de código pueden amplificar la eficacia del envenenamiento SEO. Vanilla Tempest (también conocido como VICE SPIDER o Vice Society) obtuvo más de 200 certificados fraudulentos de proveedores de confianza, como Trusted Signing, SSL.com, DigiCert y GlobalSign. Estos certificados hacían que sus instaladores maliciosos de Teams parecieran legítimos, eludiendo el software de seguridad y las sospechas de los usuarios. Los dominios de la campaña - teams-download[.]buzz, teams-install[.]run y teams-download[.]top - alcanzaron altas posiciones en las búsquedas de "descarga de Microsoft Teams" antes de la interrupción.
El objetivo de las herramientas de IA ha surgido como un tema dominante en las campañas de octubre. A medida que las organizaciones adoptan rápidamente ChatGPT, Luma AI y otras herramientas de productividad, los actores de amenazas se han posicionado para interceptar estas búsquedas. Las campañas emplean una sofisticada infraestructura basada en WordPress con scripts de huella digital del navegador que perfilan a las víctimas antes de la entrega de la carga útil. En particular, estos ataques utilizan archivos de instalación de gran tamaño (a menudo superiores a 500 MB) para eludir el análisis automatizado del sandbox, ya que muchas herramientas de seguridad omiten el análisis de archivos de gran tamaño por razones de rendimiento.
El actor de la amenaza UAT-8099, activo desde abril de 2025, ejemplifica la naturaleza de doble propósito de las modernas operaciones de envenenamiento SEO. Este grupo de habla china tiene como objetivo servidores IIS de alto valor en universidades, empresas tecnológicas y proveedores de telecomunicaciones de India, Tailandia, Vietnam, Canadá y Brasil. Al mismo tiempo que llevan a cabo el fraude SEO para obtener beneficios económicos, roban credenciales y certificados, despliegan Cobalt Strike y mantienen un acceso persistente a través de múltiples VPN y herramientas de escritorio remoto. Su fuerte seguridad operativa incluye el bloqueo de otros actores de amenazas de los sistemas comprometidos, tratando los servidores infectados como recursos exclusivos para sus operaciones.
Los ataques dirigidos a móviles representan una evolución en los requisitos de la caza proactiva de amenazas. UAT-8099 optimiza específicamente sus ataques para navegadores móviles, aprovechando el reducido espacio de pantalla que dificulta la verificación de URL. Los usuarios de móviles suelen ver las URL truncadas, lo que dificulta la detección de dominios sospechosos, mientras que la urgencia de las búsquedas móviles -a menudo realizadas mientras se solucionan problemas inmediatos- reduce la vigilancia de la seguridad.
Cómo detectar el envenenamiento SEO
El SEO poisoning se detecta identificando la cadena de comportamiento que sigue a una interacción impulsada por una búsqueda, no tratando de clasificar todas las páginas web maliciosas. Las detecciones más fiables correlacionan la actividad de referencia de búsqueda, los destinos sospechosos, las descargas o los eventos de inicio de sesión riesgosos y el comportamiento anormal de los puntos finales o las identidades en una única narrativa de investigación.
Dado que los atacantes pueden rotar rápidamente los dominios y la infraestructura, las listas de bloqueo estáticas son insuficientes. La detección debe centrarse en lo que ocurre después del clic: patrones de ejecución, mecanismos de persistencia, uso indebido de credenciales e intentos de movimiento lateral.
En términos prácticos, la detección debe responder a una pregunta: ¿Una búsqueda con alta intención provocó una ejecución anómala o un comportamiento de identidad en cuestión de minutos?
La secuencia de detección coherente es:
- Buscar referencia → dominio desconocido
- Descargar o introducir credenciales
- Ejecución anómala del proceso o emisión de tokens
- Creación persistente o tráfico saliente sospechoso
El señuelo cambia con frecuencia. El comportamiento posterior al clic no.
Indicadores técnicos de alta señal
Priorizar los indicadores que son difíciles de evitar para los atacantes y fáciles de correlacionar para los defensores:
- Anomalías del navegador al proceso: El navegador genera motores de scripts, LOLBins o cadenas de instaladores incompatibles con la navegación normal.
- Nueva persistencia poco después de la navegación: tareas programadas, claves de ejecución, servicios o elementos de inicio de sesión creados pocos minutos después de una descarga referida por una búsqueda.
- Procedencia sospechosa de la descarga: ejecutables o scripts descargados de dominios no aprobados o acortadores de URL inmediatamente después de las referencias de búsqueda.
- Anomalías en el uso de credenciales: emisión de tokens para nuevos dispositivos o sesiones, patrones de desplazamiento imposibles o acciones privilegiadas justo después de un «inicio de sesión» desde un origen no fiable.
- Comportamiento de redireccionamiento y proxy: múltiples redireccionamientos HTTP, propiedad de dominios mixtos o patrones de proxy inverso en sitios «legítimos».
Utilice la información sobre amenazas para enriquecer estas señales, pero no dependa de los IoC estáticos, ya que la infraestructura de las campañas cambia rápidamente.
Notas del sector sobre la segmentación común
El envenenamiento SEO suele seguir un comportamiento de búsqueda basado en roles, en lugar de limitarse únicamente al sector. Los atacantes dan prioridad a las consultas asociadas con la urgencia, la autoridad y el acceso privilegiado.
En los sectores regulados, este patrón se vuelve aún más pronunciado. La presión operativa, las herramientas estandarizadas y la documentación impulsada por el cumplimiento normativo crean hábitos de búsqueda repetitivos que los atacantes pueden modelar y convertir en armas.
Los siguientes ejemplos ilustran cómo las campañas de envenenamiento SEO se alinean con el comportamiento de búsqueda específico del sector y dónde debe cambiar el enfoque de la detección en consecuencia:
En todos los sectores, la ventaja para los defensores proviene del establecimiento de bases de referencia contextuales. La descarga de una herramienta o el inicio de sesión pueden ser normales en una función y anómalos en otra. Cuando la actividad referida a la búsqueda se evalúa junto con la función, el nivel de privilegios y el comportamiento de ejecución, la calidad de la señal aumenta sustancialmente.
Envenenamiento SEO y cumplimiento de la normativa
Las organizaciones deben comprender cómo se relaciona el envenenamiento SEO con diversos marcos de cumplimiento y requisitos normativos. El marcoMITRE ATT&CK clasifica específicamente el envenenamiento SEO como la técnica T1608.006 dentro de la táctica de desarrollo de recursos, destacando su papel en el ciclo de vida más amplio del ataque.
El Marco de Ciberseguridad 2.0 del NIST, con su nueva función "Gobernanza", hace hincapié en los aspectos organizativos de la defensa contra amenazas como el envenenamiento SEO. Esto incluye el establecimiento de políticas para la adquisición de software, la definición de fuentes aceptables para las descargas y la creación de procedimientos de respuesta a incidentes específicos para los ataques basados en búsquedas. La función "Identificar" del marco exige que las organizaciones mantengan inventarios de software y recursos web autorizados, mientras que la función "Proteger" impone controles de acceso que pueden impedir la instalación de software no autorizado.
Los requisitos de cumplimiento reconocen cada vez más el envenenamiento SEO como un vector de amenaza importante que requiere controles específicos. Las normativas financieras, como PCI DSS, y las sanitarias, como HIPAA, exigen implícitamente protecciones contra los métodos de distribución de malware , incluido el envenenamiento SEO, aunque puede que no nombren explícitamente la técnica. Las organizaciones deben documentar sus defensas contra el envenenamiento SEO como parte de su aplicación general de controles de seguridad.
El mapeoMITRE ATT&CK revela que el envenenamiento SEO frecuentemente se encadena con otras técnicas: T1566Phishing) para el contacto inicial, T1059 (Command and Scripting Interpreter) para la ejecución de la carga útil, T1547 (Boot or Logon Autostart Execution) para la persistencia, y T1021.001 (Remote Desktop Protocol) para el movimiento lateral. Este encadenamiento de técnicas significa que los esfuerzos de cumplimiento deben abordar todo el ciclo de vida del ataque, no sólo el vector inicial de envenenamiento SEO.
Enfoques modernos para la defensa contra la intoxicación por SEO
La industria de la ciberseguridad ha desarrollado sofisticadas contramedidas que van más allá de la detección tradicional basada en firmas para hacer frente a la amenaza del envenenamiento SEO, en constante evolución. Las estrategias de defensa modernas aprovechan la inteligencia artificial, la integración de inteligencia sobre amenazas y los cambios arquitectónicos que reducen la exposición de la superficie de ataque.
En la actualidad, las plataformas de supervisión de riesgos digitales analizan continuamente los resultados de los motores de búsqueda en busca de intentos de suplantación de marcas y de "typosquatting". Estos servicios identifican cuándo los sitios maliciosos se clasifican por los términos de marca, productos de software o servicios de una organización, lo que permite solicitar rápidamente su retirada antes de que los empleados o clientes se conviertan en víctimas. Las plataformas avanzadas utilizan el aprendizaje automático para predecir las posibles variaciones de la suplantación de identidad y vigilar preventivamente su registro.
La integración de la inteligencia sobre amenazas se ha vuelto crucial para la defensa proactiva. Los equipos de seguridad ahora pueden recibir información en tiempo real de los nuevos dominios de envenenamiento de SEO identificados, lo que permite el bloqueo automático antes de que los usuarios los encuentren. Esta inteligencia incluye no sólo nombres de dominio, sino también patrones de comportamiento, hashes de archivos e indicadores de red que ayudan a identificar campañas de envenenamiento SEO zero-day . Las organizaciones que implementan soluciones de detección y respuesta de red pueden incorporar automáticamente esta inteligencia para detectar y bloquear intentos de ataque en el perímetro de la red.
Los principios de la arquitectura de confianza cero proporcionan una defensa estructural contra las consecuencias del envenenamiento SEO. Al asumir que cualquier punto final podría verse comprometido, las implementaciones de confianza cero limitan el radio de explosión de los ataques exitosos. La microsegmentación impide el movimiento lateral, la autenticación continua bloquea el acceso no autorizado incluso desde máquinas comprometidas, y los controles de acceso de mínimo privilegio restringen lo que los atacantes pueden conseguir después de la intrusión. Este enfoque arquitectónico reconoce que algunos ataques de envenenamiento SEO tendrán éxito a pesar de los mejores esfuerzos, centrándose en minimizar el impacto en lugar de puramente en la prevención.
Vectra AI opina sobre el envenenamiento SEO
El enfoque de Vectra AI AI para la defensa contra el envenenamiento SEO se centra en la detección de comportamientos posteriores al compromiso en lugar de intentar bloquear todos los resultados de búsqueda maliciosos. La realidad es que las campañas sofisticadas de envenenamiento SEO ocasionalmente eluden las defensas perimetrales, especialmente cuando comprometen sitios legítimos o utilizanmalware zero-day . Attack Signal Intelligence se centra en identificar los comportamientos anómalos que se producen tras el ataque inicial, independientemente de cómo haya entrado el atacante.
Este enfoque conductual resulta especialmente eficaz contra el envenenamiento de SEO porque las actividades posteriores a la vulneración se mantienen constantes incluso cuando evolucionan los métodos de entrega. Ya sea que los atacantes utilicen contenido generado por IA, sitios legítimos comprometidos o un sofisticado camuflaje, eventualmente deben ejecutar cargas útiles, establecer persistencia e intentar un movimiento lateral. La plataformaVectra AI utiliza el aprendizaje automático para detectar estos comportamientos inevitables en lugar de depender de los vectores de ataque iniciales que cambian constantemente, lo que permite a las organizaciones detectar y responder a los ataques de envenenamiento SEO que, de otro modo, pasarían desapercibidos hasta que se produjeran daños significativos.
Tendencias futuras y consideraciones emergentes
El panorama de la ciberseguridad sigue evolucionando rápidamente, con el envenenamiento SEO a la cabeza de los retos emergentes. En los próximos 12-24 meses, las organizaciones deben prepararse para varios desarrollos clave que reconfigurarán la forma en que operan estos ataques y cómo deben adaptarse las defensas.
La IA generativa transformará fundamentalmente las capacidades de envenenamiento SEO para 2026. Los atacantes ya están experimentando con grandes modelos lingüísticos que pueden crear redes enteras de sitios maliciosos interconectados, cada uno con contenido único y de alta calidad que es prácticamente indistinguible de las fuentes legítimas. Estos sistemas de IA pronto serán capaces de vigilar las tendencias de búsqueda en tiempo real, generar automáticamente contenido malicioso relevante y optimizarlo para las clasificaciones de búsqueda sin intervención humana. La escalabilidad que esto proporciona significa que, en teoría, un único agente de amenazas podría envenenar los resultados de búsqueda de miles de palabras clave simultáneamente.
Los avances de la computación cuántica, aunque aún faltan años para su implantación generalizada, acabarán por romper los actuales métodos de cifrado utilizados para proteger el tráfico web. Esto creará nuevas oportunidades para los ataques de envenenamiento SEO que pueden interceptar y modificar las consultas de búsqueda y los resultados en tránsito. Las organizaciones deben empezar a planificar la implantación de la criptografía post-cuántica para mantener la integridad de las búsquedas en este panorama futuro.
Se espera que se intensifiquen las respuestas normativas a la intoxicación por SEO. La Unión Europea está estudiando enmiendas a la Ley de Servicios Digitales que responsabilizarían parcialmente a los motores de búsqueda por promover contenidos maliciosos en los resultados. En Estados Unidos y otras jurisdicciones se está debatiendo una legislación similar. Es probable que estas normativas impongan procedimientos de retirada más rápidos para los sitios maliciosos identificados y exijan a los motores de búsqueda una verificación más sólida de los resultados anunciados.
El auge de las tecnologías de búsqueda alternativas, incluidos los asistentes potenciados por IA y los motores de búsqueda descentralizados, creará nuevas superficies de ataque. A medida que los usuarios pasen de las búsquedas tradicionales en Google y Bing a pedir recomendaciones de software a ChatGPT u otros asistentes de IA, los atacantes adaptarán sus técnicas para envenenar estas nuevas fuentes de información. Esto podría incluir comprometer los datos de entrenamiento, manipular las respuestas de la IA a través de la inyección de comandos o crear plugins e integraciones maliciosas.
Las organizaciones deben priorizar varias inversiones estratégicas para prepararse ante estas amenazas en evolución. En primer lugar, deben mejorarse las capacidades de detección de comportamientos para identificar el contenido de ataque generado por IA que imita a la perfección los sitios legítimos. En segundo lugar, la formación en materia de seguridad debe evolucionar para abarcar los nuevos paradigmas de búsqueda y los asistentes de IA. En tercer lugar, los procedimientos de respuesta a incidentes deben actualizarse para hacer frente a la mayor escala y sofisticación de las futuras campañas de envenenamiento SEO.
Conclusión
El envenenamiento SEO representa un cambio fundamental en la forma en que los ciberdelincuentes abordan el acceso inicial, explotando la confianza que depositamos en los motores de búsqueda para ofrecer resultados legítimos. El panorama actual de las amenazas, ejemplificado por la Operación Rewrite de octubre de 2025, las herramientas de administración troyanizadas y las campañas impulsadas por IA, demuestra que estos ataques han evolucionado mucho más allá de la simple typosquatting para convertirse en sofisticadas operaciones de varias etapas capaces de comprometer miles de sistemas en cuestión de días.
La convergencia de contenidos generados por IA, sitios web legítimos comprometidos y técnicas de evasión avanzadas ha creado una tormenta perfecta en la que las medidas de seguridad tradicionales resultan insuficientes. Como muestra nuestra investigación, con 15.000 sitios comprometidos en campañas recientes y más de 8.500 sistemas infectados sólo a través de descargas falsas de PuTTY, las organizaciones ya no pueden confiar únicamente en las defensas perimetrales o en la formación de concienciación de los usuarios. La sofisticación de las campañas actuales, en particular las que implican certificados de firma de código legítimos y ataques al servidor como BadIIS, exige un enfoque de detección de comportamientos que identifique las actividades posteriores al ataque, independientemente del vector de infección inicial.
De cara al futuro, la integración de la IA generativa no hará sino acelerar la escala y sofisticación de los ataques de envenenamiento SEO. Las organizaciones deben adoptar una estrategia de defensa multicapa que combine controles técnicos, formación de los usuarios y, lo que es más importante, la capacidad de detectar y responder a comportamientos anómalos que indiquen que ya se ha producido un ataque. La realidad es que en una era en la que los resultados de búsqueda pueden convertirse en armas y los sitios legítimos en puntos de distribución de malware, asumir el riesgo y centrarse en la detección y respuesta rápidas se convierte no sólo en la mejor práctica, sino en algo esencial para la supervivencia.
Para los equipos de seguridad dispuestos a ir más allá de las medidas reactivas, los servicios Vectra MDR proporcionan capacidades de monitorización y respuesta experta 24/7 que pueden identificar los sutiles indicadores de comportamiento de los compromisos de envenenamiento SEO, incluso cuando las herramientas de seguridad tradicionales pasan por alto la infección inicial, lo que representa la siguiente evolución en defensa.
Fundamentos relacionados con la ciberseguridad
Preguntas frecuentes
¿Cuál es la diferencia entre el envenenamiento SEO y phishing normal?
El envenenamiento SEO difiere fundamentalmente del phishing tradicional en su enfoque de la captación de víctimas. Mientras que phishing envía activamente contenido malicioso a las víctimas potenciales a través de correo electrónico, SMS o redes sociales, el envenenamiento SEO emplea una estrategia pasiva que espera a que los usuarios busquen información específica. Esto crea una poderosa ventaja psicológica: las víctimas llegan a los sitios maliciosos con intención y urgencia, habiendo iniciado ellas mismas la interacción. Normalmente buscan soluciones a problemas inmediatos, descargas de software o documentación importante, por lo que es más probable que pasen por alto las advertencias de seguridad. Además, el envenenamiento SEO se aprovecha de la confianza implícita que los usuarios depositan en los resultados de los motores de búsqueda. Cuando alguien encuentra un sitio a través de Google o Bing, a menudo asume que ha sido investigado o verificado de alguna manera, a diferencia de un correo electrónico sospechoso que podría activar la conciencia de seguridad. La infraestructura técnica también difiere significativamente: las campañas de phishing requieren listas de correo electrónico e infraestructura de envío que pueden bloquearse o filtrarse, mientras que el envenenamiento SEO aprovecha la naturaleza abierta de la búsqueda web, por lo que es mucho más difícil de prevenir por completo. Las tasas de éxito del envenenamiento SEO a menudo superan las del phishing tradicional porque las víctimas ya están preparadas para actuar cuando llegan al sitio malicioso.
¿Pueden los antivirus detectar los ataques de envenenamiento SEO?
El software antivirus tradicional se enfrenta a importantes dificultades para detectar los ataques de envenenamiento SEO, especialmente durante las fases iniciales. Los propios sitios web no suelen contener malware , sino que pueden ser simplemente copias convincentes de sitios legítimos que recopilan credenciales o redirigen a servidores secundarios de carga útil. Las soluciones modernas de detección y respuesta en puntos finales (EDR) y de detección y respuesta ampliadas (XDR) resultan más eficaces porque analizan patrones de comportamiento en lugar de basarse únicamente en la coincidencia de firmas. Estas soluciones avanzadas pueden detectar actividades posteriores al ataque, como procesos inusuales, conexiones de red sospechosas y modificaciones no autorizadas del sistema que se producen después de la distribución malware . Sin embargo, incluso las herramientas de seguridad avanzadas tienen dificultades con las variantes demalware zero-day creadas específicamente para campañas de envenenamiento SEO. El reciente caso de abuso de certificados de Microsoft Teams demostró cómo los atacantes con certificados legítimos de firma de código pueden eludir por completo el software de seguridad. El enfoque más eficaz combina varias capas: filtrado web para bloquear dominios maliciosos conocidos, análisis de comportamiento para detectar actividades posteriores al ataque y formación de los usuarios para reconocer sitios sospechosos. Las organizaciones también deben implantar listas blancas de aplicaciones para las instalaciones de software y vigilar los indicadores de compromiso específicos de las actuales campañas de envenenamiento SEO.
¿Cuáles son los sectores más afectados por la intoxicación SEO?
La sanidad, el sector legal y los servicios financieros se sitúan sistemáticamente como los sectores más afectados por los ataques de envenenamiento SEO, y cada uno de ellos se enfrenta a patrones de amenaza únicos. Las organizaciones sanitarias son el blanco de los ataques a través de búsquedas de procedimientos médicos, información farmacéutica y software de gestión de pacientes. Los atacantes saben que los profesionales de la medicina a menudo buscan bajo presión de tiempo, lo que les hace más propensos a hacer clic en resultados maliciosos. El sector legal se enfrenta a amenazas persistentes de campañas como Gootloader, que se dirige específicamente a las búsquedas de contratos, acuerdos legales y documentación de casos. La necesidad de los bufetes de abogados de disponer de diversas plantillas de documentos y sus frecuentes búsquedas de precedentes jurídicos específicos crean numerosas oportunidades de ataque. Los servicios financieros atraen a los atacantes debido al alto valor de las credenciales comprometidas y al potencial de fraude financiero. Campañas recientes se han dirigido a búsquedas de software bancario, documentos de cumplimiento normativo y herramientas de análisis financiero. Más allá de estos objetivos principales, el panorama de amenazas de octubre de 2025 muestra un creciente interés por las empresas tecnológicas y los proveedores de servicios gestionados, especialmente a través de herramientas de administración de TI troyanizadas. Las instituciones educativas también se han convertido en objetivos principales, con universidades comprometidas para alojar infraestructura de envenenamiento SEO, mientras que al mismo tiempo son víctimas a través de búsquedas de software académico y herramientas de investigación.
¿A qué velocidad pueden escalar las campañas de envenenamiento SEO?
Las campañas de envenenamiento SEO pueden alcanzar una escala masiva con una rapidez aterradora, como demuestran incidentes recientes. La campaña de 15.000 sitios descubierta en 2024 comprometió a sus víctimas en cuestión de días, mientras que la actual campaña PuTTY/WinSCP alcanzó más de 8.500 sistemas infectados en menos de dos semanas. Esta rápida escalada se debe a varios factores. Las herramientas automatizadas permiten a los atacantes comprometer sitios web vulnerables de forma masiva: la campaña BadIIS puede infectar cientos de servidores IIS al día mediante la explotación automatizada de vulnerabilidades conocidas. La generación de contenidos mediante inteligencia artificial permite a los agresores crear miles de páginas maliciosas únicas en cuestión de horas, cada una de ellas optimizada para diferentes palabras clave y consultas de búsqueda. La infraestructura detrás de estas campañas a menudo incluye recursos de redes de bots precomprometidos que pueden activarse al instante para impulsar las clasificaciones de búsqueda a través de enlaces coordinados y generación de tráfico. Los recursos de computación Cloud permiten a los atacantes crear cientos de sitios maliciosos simultáneamente, mientras que los proveedores de alojamiento a prueba de balas garantizan que estos sitios permanezcan en línea a pesar de los intentos de desmantelamiento. La amplificación de las redes sociales y los servicios de SEO de sombrero negro pueden llevar a los sitios maliciosos a la primera página en un plazo de 24-48 horas para las palabras clave seleccionadas. Esta escalabilidad significa que cuando se descubre y analiza una campaña, miles de víctimas pueden estar ya comprometidas.
¿Qué papel desempeña la IA en el moderno envenenamiento SEO?
La inteligencia artificial se ha convertido en un multiplicador de fuerza para los ataques de envenenamiento SEO, cambiando fundamentalmente tanto la escala como la sofisticación de las campañas. Los actores de las amenazas utilizan ahora grandes modelos lingüísticos para generar contenidos web convincentes que imitan a la perfección las fuentes legítimas, con documentación técnica, testimonios de usuarios e incluso discusiones falsas en foros. Este contenido generado por IA pasa los detectores de plagio y parece original para los motores de búsqueda, lo que ayuda a los sitios maliciosos a conseguir mejores posiciones. Más allá de la creación de contenidos, los sistemas de IA analizan las tendencias de búsqueda en tiempo real, identificando palabras clave y temas emergentes a los que dirigirse antes de que los equipos de seguridad se den cuenta. Los algoritmos de aprendizaje automático optimizan el momento y la distribución de los ataques, determinando cuándo activar la infraestructura inactiva para obtener el máximo impacto. Los atacantes también utilizan la IA con fines defensivos: entrenan modelos para reconocer los comportamientos de los investigadores de seguridad y les ofrecen automáticamente contenidos benignos, mientras que atacan a los usuarios normales con malware. La sofisticación se extiende a la creación de vídeos deepfake e imágenes sintéticas que añaden credibilidad a los sitios maliciosos. A la inversa, los defensores están desarrollando sistemas basados en IA para detectar intentos de envenenamiento de SEO mediante la identificación de patrones en la generación de contenido, el análisis de anomalías en el comportamiento del sitio web y la predicción de posibles objetivos de ataque. Esto crea una carrera armamentística en la que tanto atacantes como defensores aprovechan las capacidades cada vez más sofisticadas de la IA.
¿Cómo pueden las organizaciones detectar el envenenamiento SEO en tiempo real?
La detección en tiempo real del envenenamiento SEO requiere una combinación de supervisión de la red, telemetría de puntos finales e integración de inteligencia de amenazas. Las organizaciones deben implementar la supervisión de DNS para marcar las consultas a dominios registrados recientemente, especialmente aquellos con nombres similares a software o servicios legítimos. Los registros de proxy web proporcionan una valiosa visibilidad de los datos de referencia de los motores de búsqueda, lo que permite a los equipos de seguridad identificar cuándo los usuarios llegan a sitios sospechosos a través de los resultados de búsqueda. Las plataformas de orquestación, automatización y respuesta de seguridad (SOAR) pueden correlacionar múltiples indicadores: un usuario que busca software, visita un dominio desconocido y descarga un archivo ejecutable debería activar alertas inmediatas. El análisis del comportamiento resulta especialmente eficaz, ya que supervisa patrones como las nuevas tareas programadas creadas poco después de navegar por Internet, la ejecución inesperada de PowerShell tras la descarga de archivos o las conexiones de red inusuales de software instalado recientemente. Las soluciones de análisis del comportamiento de usuarios y entidades (UEBA) pueden identificar anomalías como la descarga repentina de herramientas de administración de TI por parte de usuarios no técnicos. Los feeds de inteligencia de amenazas proporcionan actualizaciones en tiempo real sobre dominios de envenenamiento SEO recién identificados, permitiendo el bloqueo automático antes de que los usuarios los encuentren. Las organizaciones también deberían implantar cámaras de detonación o sandboxes que analicen automáticamente los archivos descargados en entornos aislados. La clave para una detección eficaz en tiempo real reside en reducir el tiempo medio de detección (MTTD) mediante la correlación automatizada de múltiples señales débiles que, en conjunto, indican amenazas de alta confianza.
¿Qué deben hacer las organizaciones si descubren un compromiso de envenenamiento SEO?
Cuando se descubre un compromiso de envenenamiento SEO, el aislamiento inmediato de los sistemas afectados es fundamental para evitar el movimiento lateral y las infecciones adicionales. En primer lugar, el equipo de respuesta a incidentes debe desconectar de la red los equipos afectados y conservarlos para su análisis forense. A continuación, identifique el vector de infección inicial revisando el historial de navegación web, los registros DNS y los registros de descargas para saber qué sitio malicioso se visitó y qué se descargó. Esta información ayuda a identificar otros sistemas potencialmente afectados que puedan haber visitado los mismos sitios. El restablecimiento de contraseñas debe ser obligatorio para todas las cuentas que estaban activas en los sistemas comprometidos, ya que el robo de credenciales es uno de los principales objetivos de muchas campañas de envenenamiento SEO. Las organizaciones deben llevar a cabo una búsqueda exhaustiva de amenazas en todo el entorno, en busca de indicadores de compromiso asociados con la campaña específica. Esto incluye la búsqueda de hashes de archivos, modificaciones del registro, tareas programadas y conexiones de red identificadas durante el análisis inicial. El análisis forense de la memoria puede revelar componentes de malware sin archivos que el análisis del disco podría pasar por alto. La recuperación requiere una reimagen completa de los sistemas afectados en lugar de la simple eliminación malware identificado, ya que los ataques sofisticados suelen incluir múltiples mecanismos de persistencia. Las actividades posteriores al incidente deben incluir la actualización de los controles de seguridad para evitar la reinfección, la notificación a las partes interesadas si se han filtrado datos y la realización de sesiones de aprendizaje para mejorar la respuesta en el futuro. Las organizaciones también deben considerar la posibilidad de contratar servicios de inteligencia sobre amenazas para saber si fueron atacadas específicamente o si se vieron atrapadas en una campaña más amplia.